Published on December 29, 2020
Installation
Install OpenVPN:
apk add openvpn
Public Key Infrastructure
Install EasyRSA:
apk add easy-rsa
Copy the template at /usr/share/easy-rsa to its own directory:
cp -a /usr/share/easy-rsa ~/certs
cd ~/certs
mv vars.example vars
Edit ~/certs/vars:
set_var EASYRSA_DN "org"
set_var EASYRSA_REQ_COUNTRY "US"
set_var EASYRSA_REQ_PROVINCE "CA"
set_var EASYRSA_REQ_CITY "SanFrancisco"
set_var EASYRSA_REQ_ORG "YourOrganization"
set_var EASYRSA_REQ_EMAIL "mail@example.com"
Set up the Public Key Infrastructure:
./easyrsa init-pki
Create the CA certificate:
./easyrsa build-ca
Generate the server certificate request and key:
./easyrsa gen-req games nopass
Sign the server certificate request:
./easyrsa sign-req server games
Generate the Diffie-Hellman parameters:
./easyrsa gen-dh
Generate the scret Hash-based message Authentication Code (HMAC):
./easyrsa --genkey --secret pki/ta.key
Upload the following files:
~/certs/pki/ca.crt=>/etc/openvpn/games/ca.crt~/certs/pki/dh.pem=>/etc/openvpn/games/dh.crt~/certs/pki/ta.key=>/etc/openvpn/games/ta.key~/certs/pki/issued/games.crt=>/etc/openvpn/games/games.crt~/certs/pki/private/games.key=>/etc/openvpn/games/games.key
Configuration
Edit /etc/openvpn/games.conf:
port 1194
proto udp
proto udp6
dev tap
user nobody
group nobody
ca /etc/openvpn/games/ca.crt
cert /etc/openvpn/games/games.crt
key /etc/openvpn/games/games.key
dh /etc/openvpn/games/dh.pem
tls-auth /etc/openvpn/games/ta.key 0
server 10.42.42.0 255.255.255.0
client-to-client
push "route 10.42.42.0 255.255.255.0"
push "route-metric 512"
push "route 0.0.0.0 0.0.0.0"
topology subnet
persist-key
ifconfig-pool-persist games-ips.txt
keepalive 10 120
comp-lzo
status /var/log/openvpn/games-status.log
log /var/log/openvpn/games.log
verb 4
mkdir -p /var/log/openvpn
chown -hR openvpn: /var/log/openvpn
Create the symlink for a game-specific service:
ln -s /etc/init.d/openvpn /etc/init.d/openvpn.games
Allow TCP traffic on port 1194:
ufw allow 1194
Start the service:
/etc/init.d/openvpn.games start
rc-update add openvpn.games
Issuing Client Certificates
Create a private key, create a certificate request and sign it for the client (replace client with a unique identifier for the client):
./easyrsa build-client-full client nopass
Edit games.ovpn:
client
dev tap
proto udp
remote example.com 1194
resolv-retry 30
nobind
persist-key
ca ca.crt
cert client.crt
key client.key
tls-auth ta.key 1
comp-lzo
status /var/log/openvpn/games-status.log
log /var/log/openvpn/games.log
verb 3
Provide the user with the following files:
~/certs/psk/ca.crt~/certs/psk/ta.key~/certs/psk/private/client.key~/certs/psk/issued/client.crt
You can then use OpenVPN to open the games.ovpn directly.
On Linux, it should also be possible to use the games.ovpn as /etc/openvpn/games.conf. Adjust the paths to the keys accordingly (e.g. by storing them in /etc/openvpn/games/). Then create symlink and run the OpenVPN service:
ln -s /etc/init.d/openvpn /etc/init.d/openvpn.games
/etc/init.d/openvpn.games start
rc-update add openvpn.games
Game Discovery
One of the problems that many games have is that when you try to find LAN games, that they will end up using the wrong network interface by default. To fix this, the VPN network interface has to be priortised over the default one. Go to Network Connections from Networking and Sharing Center. There you should see a VPN Network TAN-Windows Adapter V9 interface. Right-click it and select "Properties", you should be presented with the following window:
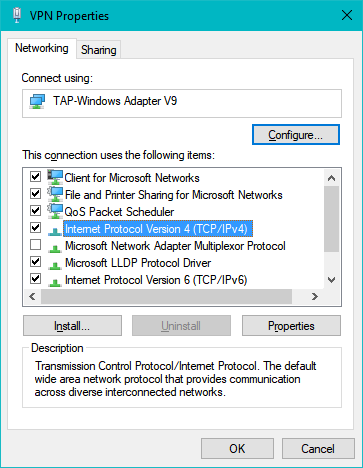
Figure 1: The VPN Properties window for the VPN Network TAN-Windows Adapter V9 interface.
Select "Internet Protocol Version 4 (TCP/IPv4)" and click on "Properties":
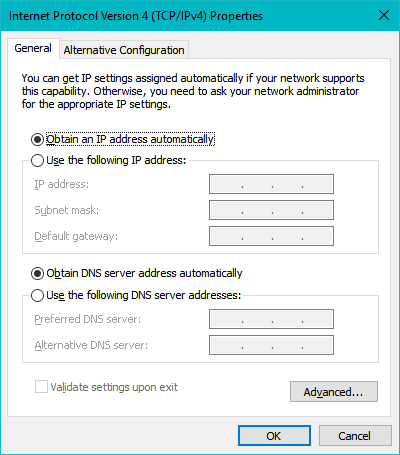
Figure 2: The Internet Protocol Version 4 Properties window.
Click on "Advanced":
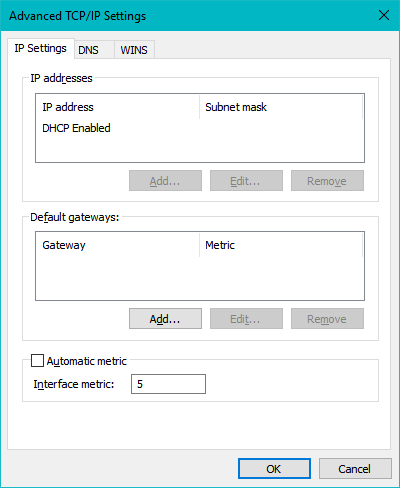
Figure 3: The Advanced TCP/IP Settings window.
Set the interface metric from automatic to manual and input 5 as its value and close the windows. Now you should be able to find your friend's hosted game using LAN discovery.
[ #alpine ]
If you like my work or if my work has been useful to you in any way, then feel free to donate me a cup of coffee. Any donation is much appreciated!